How to Secure OpenClaw for Enterprise Environments
Securing OpenClaw takes more than a firewall. Agents in production bring risks like prompt injection and supply chain attacks. This guide explains how to harden OpenClaw, set strict access controls, and meet security standards. Learn to lock down networks, audit activity, and prevent data leaks.

Understanding Agent Security Risks
Autonomous agents like OpenClaw change software security. Unlike apps that wait for input, agents act on their own to reach goals. They often have permission to read files, run commands, and use APIs. This independence is useful, but it creates risk.
The Reality of Agent Vulnerabilities Security researchers are finding serious issues. A recent analysis by Obsidian Security found that 90% of AI agents are over-permissioned. They often have more access than they need. This "excessive agency" means one compromised agent can be an entry point to your network.
Data Leakage Concerns Data privacy is the top concern for security leaders. A 2024 report by BigID notes that 81% of CISOs expressed high concerns around sensitive data being inadvertently leaked into AI training sets or external models. Without controls, an agent might upload private code to a public model or expose customer details in a debug log.
The OWASP Top 10 Context The OWASP Top 10 for LLM Applications lists risks every company should watch:
- Prompt Injection (LLM01): Attackers trick the agent to bypass rules.
- Excessive Agency (LLM08): Giving agents more permission than they need.
- Insecure Output Handling (LLM02): Running agent output without checking it.
To fix these issues, use a "zero trust" approach. Verify every action, limit every permission, and assume any agent could be compromised.
Network and Environment Hardening
Agent security starts with where the code runs. OpenClaw defaults prioritize developers, so they often expose interfaces that should be private. You must harden the host OS and network before deploying.
Bind to Localhost By default, some frameworks listen on all network interfaces. This is dangerous. Make sure your OpenClaw instance binds only to localhost. This prevents outsiders from finding and connecting to your agent's control port.
Containerization with Docker Never run OpenClaw on a host OS with root privileges. Deploy agents inside Docker containers. This limits the damage if something goes wrong. If an agent runs a bad script, the damage stays in the container and protects the host.
Strict Egress Filtering Agents need to reach specific APIs (like OpenAI, Anthropic, or Fast.io Storage) but should not have full internet access. Set firewall rules to block all inbound traffic and allow only outbound connections to approved domains. This prevents an attacker from using your agent to send data to an unknown server.
Non-Root Execution
Always run the OpenClaw process as a standard user. Create an openclaw user with no shell access and limited file permissions. This standard Linux practice stops many remote exploits.
Implementing Identity and Access Management (RBAC)
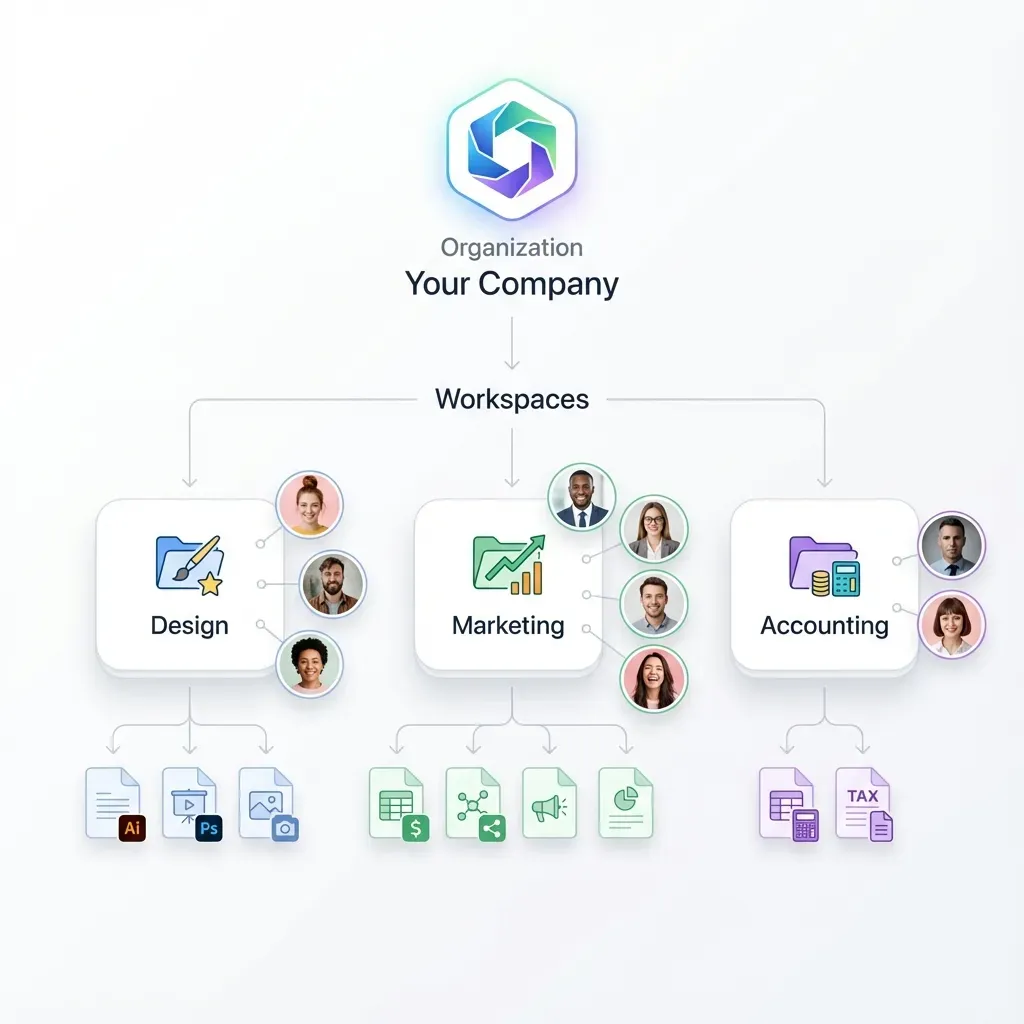
Controlling who (or what) can access your data limits potential damage. With Fast.io Workspaces, treat every agent as a user with its own login and rights.
The Principle of Least Privilege Access control failures are dangerous in AI. Without strict limits, one compromised agent can access your whole knowledge base. Permission management is your main defense against data loss.
Setting Specific Scopes Fast.io helps you limit access effectively. Instead of giving an agent a "master key," invite it to specific workspaces with limited roles:
- Viewer: For research agents that only need to read. They can search but cannot change or delete files.
- Editor: For drafting agents that write content. They can create files but should not overwrite or delete important ones.
- Admin: Keep this for humans or maintenance scripts that need full control.
By setting permissions at the workspace level, you ensure a compromised agent in "Marketing" cannot touch files in "HR" or "Finance." This separation secures your data.
Securing the Agent Supply Chain
Treat agent configs and prompts like code. A secure supply chain stops unverified changes from reaching production.
Automated Prompt Testing Test prompts like you test code. In your CI pipeline, add a step that tries common jailbreaks against your agent. If the agent fails a "DAN" (Do Anything Now) attack, the build should fail.
Secret Scanning in Repositories
Developers often commit API keys to Git by mistake. Use tools like trufflehog or GitHub Advanced Security to block commits with keys. This stops leaks at the source.
Immutable Infrastructure Deploy agents as fixed units. Instead of updating an agent's config on the server, rebuild the Docker image and redeploy it. This keeps your production environment clean and prevents security settings from degrading over time.
Dependency Scanning Agents often use Python or Node.js libraries that may have bugs. Use Software Composition Analysis (SCA) tools to scan dependencies for known issues. Block builds with serious vulnerabilities to stop supply chain attacks.
Data Protection and Encryption Strategies
Enterprise use requires protecting data at rest and in transit. Fast.io provides a secure layer that works with OpenClaw to keep intellectual property safe.
Encryption Standards Fast.io uses industry-standard AES encryption for stored files and modern TLS for data in transit. Even if someone stole the physical drive, they could not read the data. This encryption is essential for finance or healthcare compliance.
Eliminating Local Data Risks A common security gap happens when agents download files to process them. This leaves copies of data in temporary containers. Fast.io's URL Import feature lets OpenClaw pull files from cloud sources (like Google Drive, OneDrive, or Dropbox) into the secure workspace without writing to the local disk.
Secure Data Rooms for High-Stakes Projects For mergers or confidential launches, standard workspaces may not be enough. Fast.io Data Rooms offer more control:
- Dynamic Watermarking: Adds user identity to document previews to stop screenshots.
- Expiration Policies: Removes access to shared links after a set time.
- Domain Whitelisting: Limits access to users from specific email domains.
Learn more about these features on our AI Product Page.

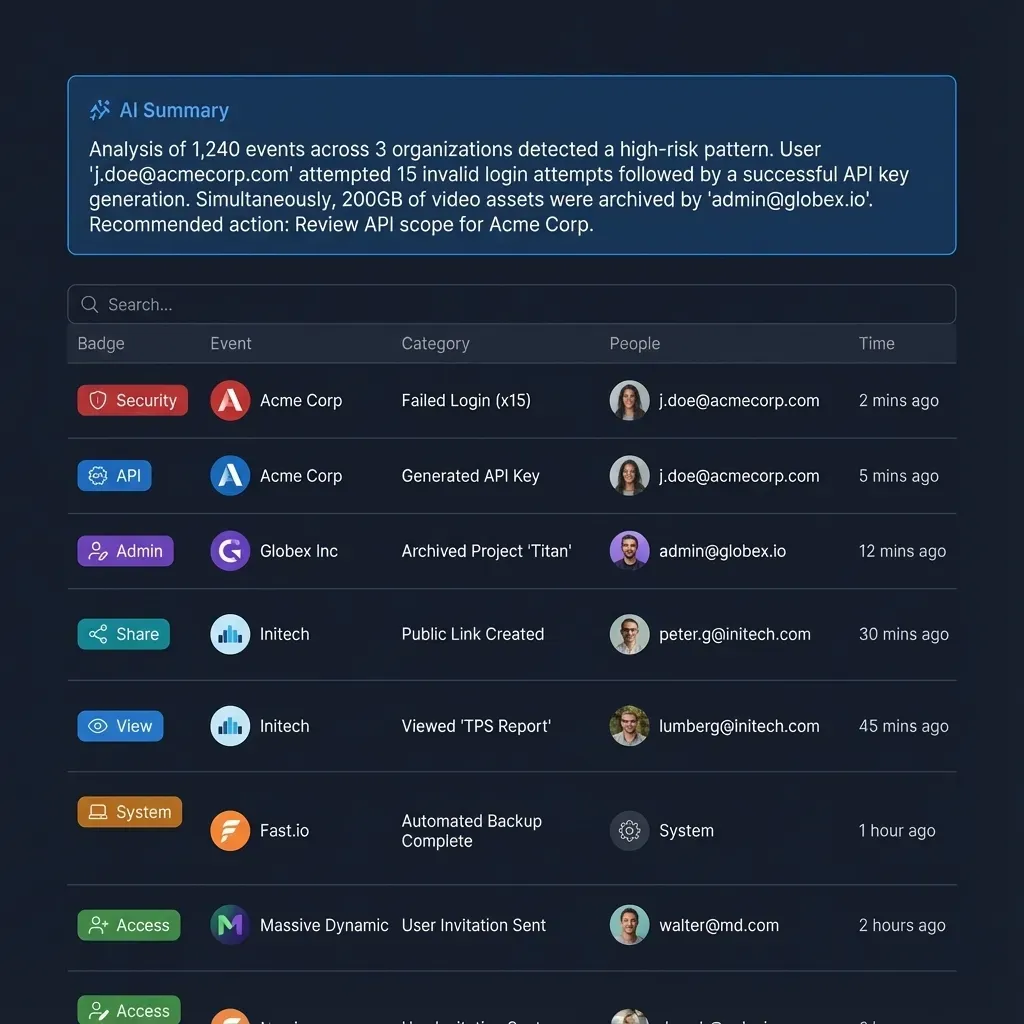
Audit Logging and Threat Detection
You can't secure what you can't see. Visibility is your safety net. Audit logging lets security teams see what happened, find the cause of problems, and prove compliance.
What to Monitor in Agent Logs Monitoring is more than tracking errors. Set your SIEM system to flag specific OpenClaw activity:
- High-Volume File Access: A spike in file reads (e.g., opening a large volume of files in a short time) could mean data theft.
- Unusual Tool Execution: If a "Research Agent" tries to use a "System Command" tool, that is a strong warning sign.
- Permission Changes: Any attempt by an agent to change its permissions or create keys should trigger an alert.
Fast.io's Agent Storage includes audit trails that log every action. You can use Webhooks to stream these logs to your tools for real-time detection.
Vetting and Managing Third-Party Skills
OpenClaw lets you add skills, but third-party code brings risk. A bad skill could steal keys, mine crypto, or send data to an outside server.
Skill Vetting Framework Before installing a new skill, check it carefully:
- Source Verification: Only install skills from verified publishers. Be careful with new accounts that have no history.
- Code Review: Read the
SKILL.mdfile and the source code. Look for hidden code, strange network requests, or hardcoded passwords. - Sandboxed Testing: Never deploy a new skill to production right away. Test it in an isolated place first.
For file management, using unverified tools is risky. We recommend the official Fast.io ClawHub skill (dbalve/fast-io). This skill gives OpenClaw a secure way to work with Fast.io Agent Storage, ensuring all actions are logged and follow your rules.
Data Loss Prevention (DLP) for Agents
Preventing sensitive data from leaving your network is your final defense. Agents process lots of text, so PII (Personally Identifiable Information) or secrets can leak into prompts or outputs.
PII Redaction Techniques
Before an agent sends text to an LLM, it should pass through a redaction layer. Tools like Microsoft Presidio or Google DLP API can find and mask names, phone numbers, and emails. By replacing John Doe with <PERSON> before the prompt leaves your network, the model provider never sees the real data.
Output Filtering Use a filter to scan agent responses for sensitive patterns before showing them. Regular expressions can catch credit card numbers, social security numbers, and API keys.
Context Awareness Make sure your agents know their context. An agent in a "Public" workspace should not access docs in a "Confidential" workspace. Fast.io's workspace isolation enforces this, stopping leaks between contexts.
Human-in-the-Loop (HITL) Controls
For high-risk actions, do not let automation run alone. Human-in-the-Loop (HITL) controls make sure humans approve critical decisions.
Approval Workflows Set your agent to pause and ask for approval on sensitive tasks. For example, an agent might draft an email, but a human must click "Approve" to send it. Code from an agent should go through a Pull Request before merging.
Rate Limiting Set limits on agent actions. If an agent tries to delete a significant number of files in a short time or send a high volume of emails, the system should lock the account and alert an admin. This prevents runaway scripts or bad actors from causing damage.
Frequently Asked Questions
Is OpenClaw SOC2 compliant?
OpenClaw is open-source and does not hold SOC2 certification. However, Fast.io provides the security layer, including encryption, access controls, and audit logs, that helps teams meet SOC2 requirements when deploying agents.
How do I prevent OpenClaw from deleting files?
The best way is to use Fast.io's RBAC system. Give the agent a 'Viewer' or 'Contributor' role. These roles block file deletion, making accidental or malicious commands harmless.
Can I run OpenClaw behind a corporate firewall?
Yes, OpenClaw works in restricted networks. Configure your firewall to allow outbound HTTPS connections to the APIs your agent needs (like OpenAI or Fast.io) while blocking unauthorized inbound traffic.
How does Fast.io protect agent data at rest?
Fast.io encrypts data at rest with industry-standard AES encryption. Workspaces are isolated, so data from one workspace cannot be accessed by agents or users in another without permission.
What is the safest way to store API keys for OpenClaw?
Never hardcode API keys in config files. Use environment variables or a secrets manager like AWS Secrets Manager or HashiCorp Vault. Inject these secrets into the container at runtime.
How can I detect if my agent has been compromised?
Watch audit logs for odd file access, use of unauthorized tools, or connections to unknown IPs. Fast.io's activity logs help you spot these signs early.
Related Resources

Secure Your Agent Workforce
Give your OpenClaw agents a secure, monitored home with granular permissions, audit logs, and enterprise-grade encryption.